- What is a Replay Attack?
- How Do Replay Attacks Work?
- Is Replay Attacks Applicable to WordPress Site Security?
- Common Targets of Replay Attacks on WordPress Sites
- Securing Your WordPress Site Against Replay Attacks
- 1. Enforce HTTPS Across Your WordPress Site
- 2. Implement Nonce Tokens to Validate Requests
- 3. Adopt Strong Session Management and Expiration Policies
- 4. Multi-Factor Authentication (MFA) as a Layer of Security
- 5. Regular Updates for WordPress, Plugins, and Themes
- 6. Limit Access and Role-Based Permissions
- 7. Enable Logging and Activity Monitoring
- Advanced Security Measures to Thwart Replay Attacks
- Conclusion
- FAQs
Is Replay Attacks Applicable to WordPress Site?
- What is a Replay Attack?
- How Do Replay Attacks Work?
- Is Replay Attacks Applicable to WordPress Site Security?
- Common Targets of Replay Attacks on WordPress Sites
- Securing Your WordPress Site Against Replay Attacks
- 1. Enforce HTTPS Across Your WordPress Site
- 2. Implement Nonce Tokens to Validate Requests
- 3. Adopt Strong Session Management and Expiration Policies
- 4. Multi-Factor Authentication (MFA) as a Layer of Security
- 5. Regular Updates for WordPress, Plugins, and Themes
- 6. Limit Access and Role-Based Permissions
- 7. Enable Logging and Activity Monitoring
- Advanced Security Measures to Thwart Replay Attacks
- Conclusion
- FAQs
In the constantly evolving world of cybersecurity, new threats are always emerging, placing websites and sensitive data at risk.
One such often overlooked threat is the replay attack. As WordPress remains the most widely used content management system (CMS), the question arises: Is replay attacks applicable to WordPress site?
Understanding what replay attacks are, how they might affect WordPress sites, and what specific steps you can take to prevent them are essential to safeguarding your website and user data.
In this comprehensive guide, we’ll explore the fundamentals of replay attacks, examine whether they are truly relevant to WordPress, and share effective strategies to secure your site.
What is a Replay Attack?
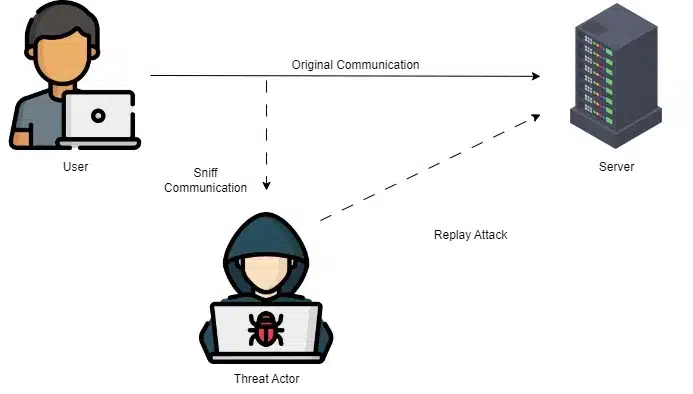
A replay attack is a network attack in which the attacker intercepts a legitimate data transmission and “Attacks Applicable to WordPress Site” it, tricking the receiving system into accepting it as a valid request.
This is particularly dangerous because replay attacks are not required to have a motive to decrypt any data to be used against the functionality of any website.
For the website owner asking, “Are replay attacks applicable to WordPress site functionality?” understanding the mechanics of replay attacks is fundamental.
In a nutshell, replay attacks entail interception of login credentials, session tokens, or even payment information while they are being transmitted.
his information can then be “replayed” so that the attacker appears as the legitimate user and gains access to your site without directly breaking encryption algorithms.
How Do Replay Attacks Work?
Let’s dissect the process in a WordPress site replay attack so that we can understand better whether this can be applied:
- Data Transmission Interception: An attacker waits for an unsecured data transmission on the network.
- Catching Authentication Data: The attackers catch important information like session tokens or API keys.
- Replay of the Captured Data: The attacker sends these captured data back to the server, impersonating the original user, and getting unauthorized access.
Replay attacks are much more dangerous if WordPress sites do not differentiate between variables, timestamps, and proper session handling mechanisms that would keep submitting of the same information from being submitted on multiple occasions.
Is Replay Attacks Applicable to WordPress Site Security?

Given that WordPress runs an exorbitant portion of the internet, many site owners wonder if replay attacks are applicable to the security of a WordPress site in practice.
The answer is complex and depends upon security settings, the plugins used, and the warnings given by the site owner. Here are a few ways in which replay attacks could indeed be applicable to a WordPress site:
- Lack of HTTPS Encryption: It means that data transmitted in WordPress sites that are still on HTTP can be intercepted. This would make attackers able to capture and reuse data transmissions, which could thus be used to mount replay attacks, among others.
- Flawed Token Management in WordPress Plugins: Most WordPress plugins use token-based authentication for user sessions or connections to APIs. If tokens are not provided with an expiry time, it again opens avenues for reuse of those for a replay attack.
- Lack of Multi-Factor Authentication (MFA): Since multi-factor authentication is the best defense against replay attacks, without this feature, attackers would use the intercepted data and take the identity of users.
- Outdated Plugins and Themes: Updated plugins are significant, but when not properly updated, outdated plugins may not hold the wanted security update that stops replay attacks.
- Weak or Misconfigured Authentication Plugins: Weakly configured authentication plugins may be vulnerable to leaving session data open to replay attempts.
Common Targets of Replay Attacks on WordPress Sites

Identifying such commonly targeted points will help us assess whether replay attacks are applicable to the security of WordPress sites. Commonly targeted points in a replay attack against WordPress are as follows:
1. Login Authentication
The replay attack mechanism is generally pointed at WordPress login authentication mainly because login pages lack protection through HTTPS or robust token management.
Obtaining login session information from attackers might evolve into an attempt to utilize the retrieved information to access users’ accounts.
2. APIs and Plugin Endpoints
Most plugins depend on WordPress functionality through APIs and hence become quite easy targets.
When requests eventually reach the APIs and are either unencrypted or do not use secure tokens, it becomes easy for them to replay them to achieve unauthorized actions.
3. Ecommerce Transactions
In the case of eCommerce sites on WordPress with plugins like WooCommerce, replay attacks may lead to duplicated transactions, unauthorized purchases, and potential exposure of customer information. This is not great news for both the business and customers.
4. Submissions of User Data
The types of forms that are liable to replay attacks, as well as interception, are subscription or registration forms.
Because of this, confusion among suitable replay attacks for the features of your WordPress website, spam, and security breach problems can result in these forms.
5. Accessing the Admin Panel
If session tokens are not stringently controlled when you deal with them, an admin session can be intercepted and used for replay attacks.
This means unauthenticated access. It then becomes possible for the attacker to gain control over settings of the site.
Securing Your WordPress Site Against Replay Attacks
Now that we’ve established Is replay attacks applicable to WordPress site vulnerabilities, it’s time to dive into methods for securing your site against these risks.
1. Enforce HTTPS Across Your WordPress Site
Your WordPress site needs to ensure https for the transmitted data so that the attacker cannot alter it in the communication between client and server.
- How to enable HTTPS in WordPress: By utilizing an SSL certificate from reliable providers like Let’s Encrypt, Cloudflare, or hosting providers.
- Benefits of HTTPS: In addition to preventing replay attacks, making use of HTTPS enhances your ranking in search engines and gives your site a security element that it offers to your visitors.
2. Implement Nonce Tokens to Validate Requests
WordPress also has some built-in nonce functions like wp_nonce_field() and wp_verify_nonce(), which generate one-time tokens for forms and actions, ensuring that any request received is unique and not replayed; hence, there are no replay attacks.
- How Nonces Work: Generally, a nonce is generated by a form or action. WordPress checks the nonce during the execution of the submission request. If it does not find an existing nonce, WordPress will reject the request.
- Best Practices: Never send nonces with sensitive operations, such as form submission, AJAX requests, or API calls.
3. Adopt Strong Session Management and Expiration Policies
Proper management of sessions eliminates the possibility of replay attacks, making intercepted sessions useless after a definite time period.
- Session Expiry: Sessions expire within an interval; the smaller it is, the less time one can use intercepted sessions.
- Session Regeneration: Use plugins or custom solutions to refresh session IDs at login, making caught data useless.
4. Multi-Factor Authentication (MFA) as a Layer of Security
MFA stands for Multi-Factor Authentication, and one of the powerful defenses for WordPress sites would be this. It adds a second layer to logins that no attacker will bypass easily.
- Best MFA Plugins for WordPress: Good plugins for MFA include Google Authenticator, Duo, and Wordfence, as they do not get too difficult to implement.
- Why MFA Prevents Replay Attacks: Even if login credentials are intercepted, the attacker cannot log in without the second authentication factor.
5. Regular Updates for WordPress, Plugins, and Themes
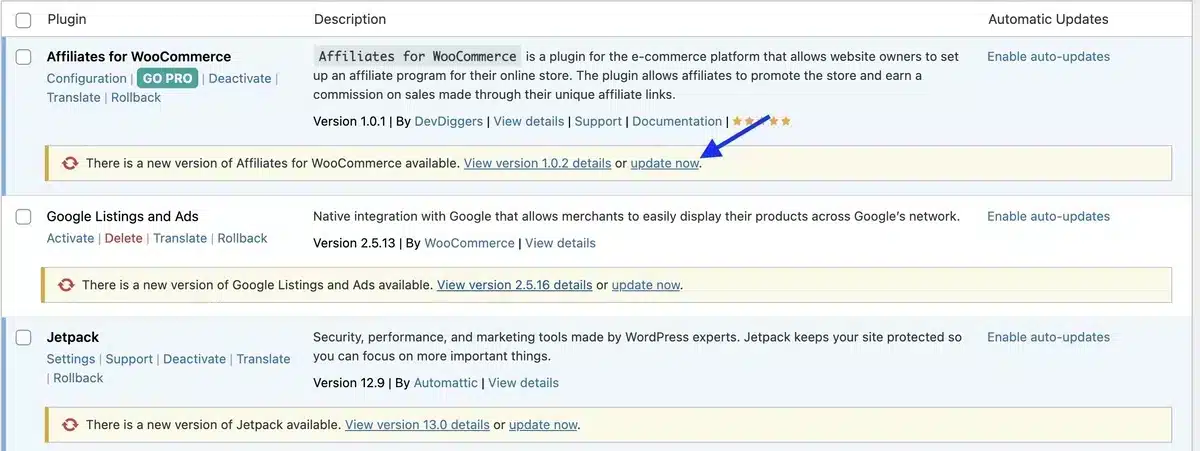
Updating your WordPress installation and its plugins is essential for site security. Most of the time, updates carry patches against vulnerabilities that can be used by attackers.
- Automatic Update: Activate automatic updating for the plugins and themes.
- Caution in Installation of Plugins: Only use trusted plugins from good developers. Plugins that are poorly maintained will have more vulnerability.
6. Limit Access and Role-Based Permissions
Restrict permissions of users to allow access being leveraged against your website.
Assign the most appropriate ones; thus, for managing critical areas of your website, this is highly indispensable for them.
- Assign Suitable Roles: WordPress has its built-in roles where users will be granted access as positioned by the role of each user.
- Role-management plugins: By using User Role Editor or other similar plugins that allow for granular control over user permissions.
7. Enable Logging and Activity Monitoring
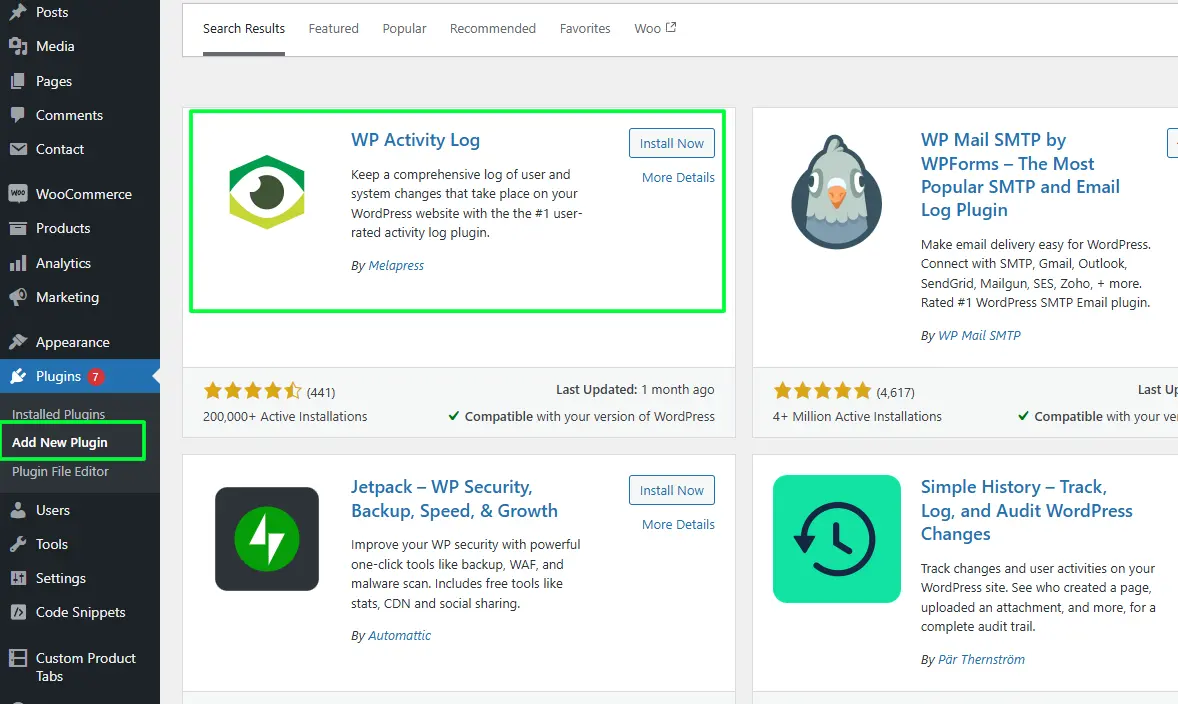
Configuration of logs and activity checking of the user can identify suspicious patterns in advance, thus replay attacks are detected much before a crime occurs.
- Activity Logging Plugins: To track login attempts, unsuccessful login attempts, form submissions, and API access, use WP Activity Log or any such plugin.
- Real-Time Alerts: Several security plugins provide real-time alerts-you will know right away if some funny business is going on on your site.
Advanced Security Measures to Thwart Replay Attacks
For enhanced security on the WordPress site, a few advanced techniques prevent replay attacks:
- Turn on encryption for cookies: Session information will be better encrypted – which in turn reduces interception of the session.
- Use rate limiting based on IP or restrict: Limit access attempts from a single IP address. Tools like Fail2Ban or Cloudflare can easily enforce such restrictions. This becomes a significant challenge for attackers to launch replay attacks.
- Content Security Policy (CSP): A Content Security Policy is used to implement the control of where and how data are being sent, thus adding an additional layer of protection against malicious actors that can intercept and replay the data.
- HSTS or HTTP Strict Transport Security: When the HSTS is enabled, the only connection that browsers make will be over HTTPS; it guards against man-in-the-middle attacks, which further leads to replay attacks.
- Nonce Tokens for Sensitive Actions: Nonce should be used in requests for form submissions and actions: each nonce is, therefore, unique and cannot be replayed. It is especially effective for sensitive actions such as login update transactions, etc.
Conclusion
In a nutshell, do replay attacks apply to the security provided on a WordPress website? It can be yes, but specific precautions minimize the risk of it.
For a WordPress website owner, proactive security practices like HTTPS, nonce tokens, MFA, session management, and continuous monitoring go a long way in preventing replay attacks.
No website in this world is 100% secure from cyber attacks, but caution and multiple layers of security do make your WordPress website highly resistant to replay attacks and other varieties of risks.
FAQs
What exactly is a replay attack?
A replay attack is a type of cyberattack where an attacker intercepts data (like login credentials or session tokens) and retransmits it to impersonate a user and gain unauthorized access without decrypting the data.
Is replay attacks applicable to WordPress site security?
Yes, replay attacks can impact WordPress sites, especially if security measures like HTTPS, nonce tokens, or multi-factor authentication (MFA) are not implemented.
How can I protect my WordPress site from replay attacks?
Key protections include enforcing HTTPS, using nonce tokens for form and action validation, enabling MFA for logins, and regularly updating plugins, themes, and WordPress itself.
Are replay attacks common on WordPress sites?
While replay attacks aren’t the most common threat, WordPress sites lacking robust security protocols are still vulnerable. Attackers typically exploit sites with outdated security practices or unencrypted connections.
Does using HTTPS protect my WordPress site from replay attacks?
Yes, HTTPS encrypts data in transit, making it significantly harder for attackers to intercept and reuse it. It’s a crucial first step in defending against replay attacks.

Abhijit Sarkar
Hi, I’m Abhijit Sarkar. I am deeply passionate about creating engaging content and exploring. My journey includes gaining valuable experience in content writing and creating useful resources for my readers.

Leave a Reply