How Do Hackers Mine WordPress for Admin Email Addresses?
WordPress powers over 40% of websites in today’s digital world, making it a prime target for cybercriminals. One of the key tactics hackers use to gain control of a site is mining for admin email addresses.
But how do hackers mine WordPress for admin email addresses, and why is this information so valuable?
Admin emails are often the gateway to sensitive information, account control, and even full site access.
Understanding hackers’ methods and the reasons behind targeting admin emails is crucial to safeguarding your WordPress site from attacks.
Why Hackers Target Admin Email Addresses

Admin email addresses tend to be a source of much power.
Generally, they are linked with the site’s most authoritative accounts and are frequently used in account recovery and password reset functions.
Assuming that hackers gain an admin email, they can carry out the following actions:
- Send spam e-mails: Those requiring the recipient to spill sensitive information such as passwords.
- Initiate brute force attacks: using the e-mail to try out different password combinations until one of them works.
- Reset Passwords: Most WordPress sites allow resetting of passwords via an email link; thus, access to the email is effectively a means to access the admin account.
- Exploit Social Engineering: Pose as the legitimate admin and coerce support teams or third-party service providers into giving up further details of or access to the site.
- Bypass Two-Factor Authentication: The sender will get 2FA and, consequently, bypass the additional security layer to take over the account because hackers now have access to the admin’s email.
So, how do hackers mine WordPress by extracting admin email addresses? Let’s find out.
How Do Hackers Mine WordPress for Admin Email Addresses: Common Methods
1. Using Default WordPress Features

One of the easiest ways hackers exploit to obtain admin email addresses is by exploiting WordPress default features.
When installing WordPress, some configurations can display sensitive information. Here is how it works:
Author Archives URL
Each WordPress user has an author page, which is typically crawled by search engines. Hackers can then visit this page and see the admin username, which is usually a pretty clear indication of the admin email address.
Consider if the WordPress admin username happens to be the same as the email prefix, such as the username john.doe and email john.doe@example.com; hackers would readily guess at the full admin email address.
WordPress Login Error Messages
Sometimes, a guessed email may well try to log in with WordPress, revealing whether that email address exists or not.
When an error message such as “This email is not registered” shows up then it simply means the email was wrong and “Incorrect password” implies the email actually existed.
Thus, a hacker could try multiple times by using a different email and keep going until they get the right one.
2. Using the WordPress REST API
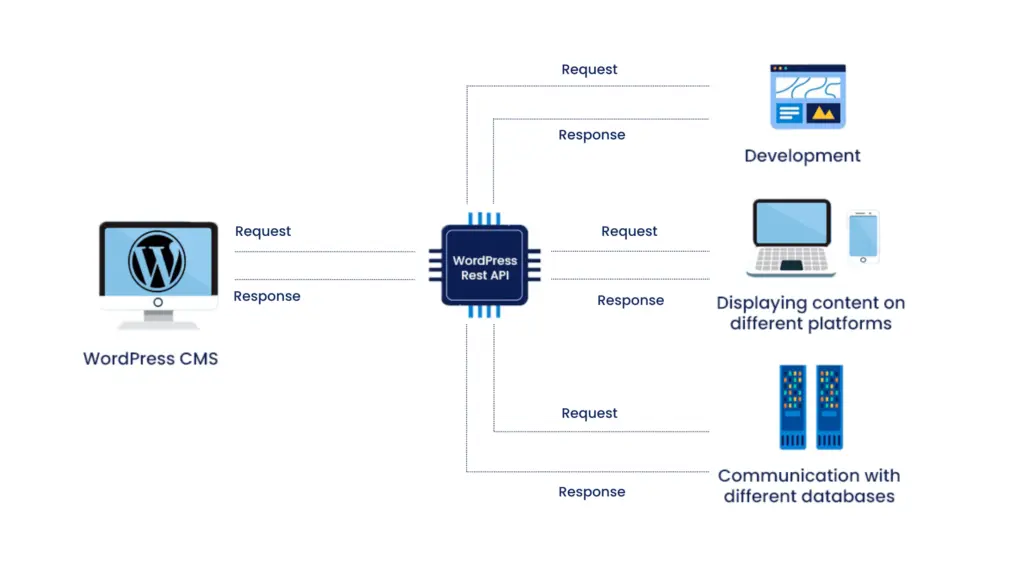
The WordPress REST API is an incredibly powerful tool for developers, allowing access to various website data via HTTP requests. However, it can also be misused by hackers to expose sensitive details.
The REST API allows users to list registered users on a WordPress site, and if not properly secured, it can reveal admin details, including their email addresses. Hackers can craft API requests like:
/wp-json/wp/v2/users
This request can return a list of users, including admin accounts, sometimes displaying email addresses or usernames that closely resemble emails.
3. Scraping Contact Forms
Most WordPress sites will have some contact form where administrators’ emails have been listed in a public manner for ease of communication.
Though well-meaning, hackers are using automated tools to crawl these pages to harvest email addresses.
Although the email won’t be shown, hidden input fields or scripts with the email address can still be scraped.
4. Exploiting Vulnerable Plugins and Themes
WordPress has many plugins and themes available to customize the look and functionality of a site, but those plugins and themes are pretty bad sources of vulnerabilities; in fact, so many outdated or poorly coded plugins and themes expose the details of users and even admin email addresses.
Many hackers scan through websites in search of these vulnerabilities. If they find a plugin that hasn’t been updated for ages or has a known security flaw, that’s the chance they exploit and steal passwords.
For instance, a cracked plugin can allow access to the WordPress dashboard or database, which contains email addresses of the administrators.
5. SQL Injection Attacks

SQL injection is an attack whereby hackers input malicious SQL commands within forms or even URLs, to access a website’s database.
This SQLi-vulnerable WordPress allows hackers to manipulate their databases and extract sensitive information, for instance, admin email addresses.
Websites that use older versions of WordPress or Plugins or themes are at a greater risk as some updates might not have to patch for such attacks.
6. Brute Force Attacks on Login Forms
Brute-force attacks and brute-force password cracking operate on the basis of systematically trying out all possible combinations of emails and passwords until they finds the right one.
Hackers start off by first identifying a valid admin email address and then use automated tools to attempt thousands of logins per minute. Once they know the correct email, they can settle down to cracking the password using a brute-force method.
Even though CAPTCHA has been provided on the site as a security measure for brute force protection, hackers are likely to circumvent it with more complex tools that emulate human actions.
7. Social Engineering
Not everything is technical hacking. Social engineering is a psychological manipulation whereby people are confused about providing sensitive information. Hackers often pretend to be other legitimate users or providers to obtain admin emails.
For example, they may contact the hosting provider for a website claiming themselves to be its admin and requesting email details. They can also send phishing emails to other site users claiming they need their help in “fixing” something and ask for admin emails in the course of the process.
8. Exploiting Email Disclosure via Source Code
Sometimes, WordPress admins unknowingly expose their email addresses in the HTML source code of their website due to:
- The email is hardcoded into the theme or plugin files.
- The email is listed in meta tags for SEO reasons.
- The admin email is part of the comments and feedback sections.
Hackers can just open the source code for any page and scroll down to find common email addresses like @example.com.
This is best when the email is only present in the source code but is not visible through the user interface.
How to Secure Your WordPress Site from Hackers
Now that we understand how hackers mine WordPress for admin email addresses.
Let’s explore actionable steps you can take to secure your site.
1. Hide Admin Email in the WordPress Dashboard
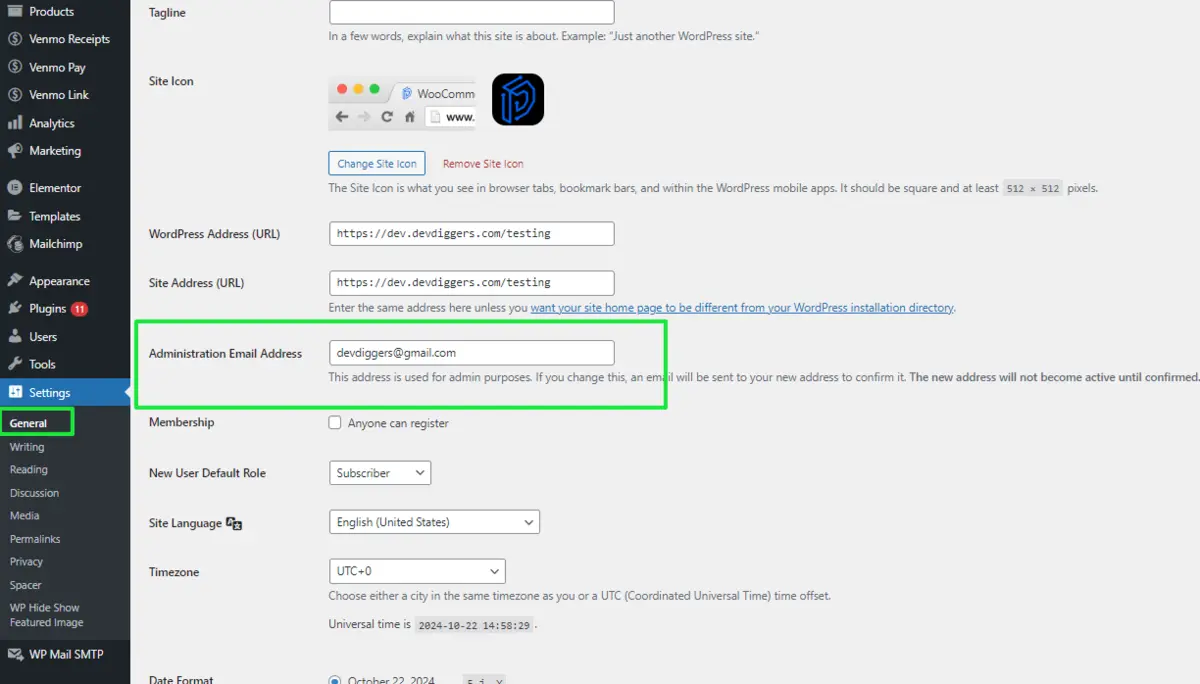
The most straightforward first step is to avoid using the default WordPress settings that expose admin details.
Make sure your admin account username and email aren’t the same.
Also, refrain from displaying admin details on author archives, contact forms, and public pages.
Consider installing plugins, such as Edit Author Slug, which will allow you to change the author slug for something less predictable than the username, making it harder for hackers to guess your admin emails.
2. Disable the WordPress REST API
If your site doesn’t need the WordPress REST API, it’s best to disable it. You can do this through various security plugins or by adding code to your theme’s functions.php file:
add_filter('rest_authentication_errors', function($result) {
if (!empty($result)) {
return $result;
}
if (!is_user_logged_in()) {
return new WP_Error('rest_not_logged_in', 'You are not currently logged in.', array('status' => 401));
}
return $result;
});This code snippet disables the REST API for non-logged-in users, preventing hackers from accessing user data through the API.
3. Use Security Plugins
A security plugin like Wordfence or Sucuri would prevent many hits against your site.
These kinds of plugins watch over login attempts, block brute-force attacks, and even alert you if someone is trying to mine email addresses using pretty unorthodox methods.
These types of plugins also:
- Limit Login Attempts: Limit the number of failed login attempts coming from the same IP.
- Scan for Vulnerabilities: Pinpoint outdated plugins and themes that need updates.
- Monitor Change: It will notify you of any changes in the core files that indicate a breach.
4. Update WordPress, Plugins, and Themes Regularly
Updates are the most important. Hackers are always trying to find out the weak spots in outdated versions of WordPress, plugins, or themes.
You should maintain your website to update known security issues.
5. Implement CAPTCHA and 2FA (Two-Factor Authentication)
CAPTCHA plugin addresses automated brute force attacks, and the Two-Factor Authentication (2FA) plugin enhances the security of logging in.
In case a hacker guesses your admin email, he will not succeed without the use of the second factor, which happens to be a one-time code sent either to your cell phone or email address.
Most of the security plugins have 2FA options that are easy to set up and use.
6. Use Strong, Unique Passwords
Use strong, unique passwords on the account in the admin and other accounts linked to your website in WordPress.
In case you want highly simple accounts such as “admin123” or with personal data that someone can guess, use them at your own risk.
You may use password managers like LastPass or Bitwarden for easy generation of complex unique passwords to be stored elsewhere.
7. Remove Unnecessary Users
If your WordPress website is multisite, ensure only those users who need to be administrators have the account set as such.
Many sites collect dust and cobwebs with inactive user accounts that are still around but no longer contribute to the website but have elevated privileges.
Clean those out regularly from your attack surface.
8. Monitor Logs and Activity
Monitoring your site’s logs and user activity will catch suspicious behaviour before it becomes a problem.
Most security plugins include such functionality as an activity log that tracks all login attempts, file changes, and other critical actions.
You could also manually scan server logs for signs of brute force attacks or repeated requests to certain pages, indicating the hackers are essentially mining information from your site.
Conclusion
The question is: “How do hackers mine WordPress for admin email addresses?”
Seriously, all WordPress site owners should take it.
All that hackers need is a combination of default WordPress features, brute force attacks, and vulnerabilities in plugins and themes to get your admin email address.
So, with proper security in place—including disabling unnecessary features, setting good passwords, adding 2FA, and keeping your site up to date—you make it much harder for the hackers to be successful. Remember, proactive defence is always better than reactive recovery.
Take action today to protect your WordPress site and prevent that admin email from falling into unwanted hands.
FAQs
Why do hackers target admin email addresses on WordPress?
Hackers target admin emails to gain access to password resets, control the website, and exploit sensitive information.
How do hackers mine WordPress for admin email addresses?
Hackers use methods like author pages, directory listings, brute force attacks, and vulnerable plugins to find admin emails.
Can hackers bypass two-factor authentication with admin emails?
Yes, if hackers gain access to the admin email, they can intercept 2FA codes and bypass this security layer.
What is the risk of exposing admin email addresses?
Exposed admin emails can lead to phishing attacks, account hijacking, and full website takeovers by hackers.
How can I protect my WordPress admin email address?
Use strong passwords, enable two-factor authentication, hide admin email addresses, and keep plugins updated to secure your site.

Abhijit Sarkar
Hi, I’m Abhijit Sarkar. I am deeply passionate about creating engaging content and exploring. My journey includes gaining valuable experience in content writing and creating useful resources for my readers.

Leave a Reply